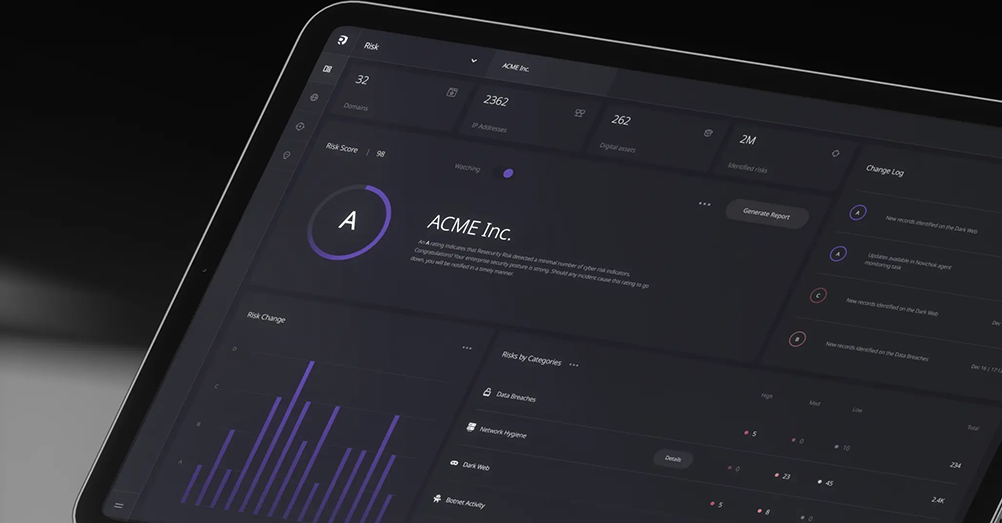
Risk™
Description
Time is our most valuable resource in cybersecurity. Leverage Risk™ to automate your digital risk management and receive insight about any significant changes to your security posture due to Dark Web, data breach, compromised credentials, network infections and other security incidents.
- In-depth risk evaluation of the entire enterprise.
- Early-warning security notifications.
- Automated daily security posture reports.
- Data is displayed on a convenient dashboard.
Measure Risk To Control Your Enterprise Security Posture
- Accurate
- Scalable
- Effective
In-depth risk evaluation throughout the entire enterprise ecosystem.
Monitor digital footprints of any size on a massive scale.
Proactively enabling strategic actions to improve security.
Capabilities
Measure Risk
Your daily security score is rated based upon a summary of all risks for your monitored domains, IPs, networks, vulnerabilities, and cloud services. Actionable intelligence with immediate remediation is key to achieving a high security score.
- Unparalleled risk management
- Actionable intelligence that makes a difference
Risk Assessment
Refine and enrich datapoints to understand where weaknesses and vulnerabilities in your digital assets are. Changes and updates are sent through notifications via reports or e-mail as new data is discovered.
Risk Categories
Identify external threats based upon high-quality intelligence aggregated from over 20,000 public and closed sources.
External Risk vectors:
- Account Takeover
- Botnet infections
- Business E-mail Compromise
- Cyberespionage
- Brand Reputation Abuse
- Dark Web Activity
- Domain Squatting
- Data Breaches
- Digital Certificates
- Exposed Network Services
Internal Risk vectors:
- Active Directory Account Compromises
- Backdoors
- Incorrect Network Segmentation
- Security Anomalies
- Lateral Movement
- Malicious Traffic
- Vulnerable Software
- Misconfiguration Errors
- Unpatched Services
Cloud Risk vectors:
- Abandoned EC2 instances
- Exposed Databases
- Compromised Credentials
- Sensitive Data Identification
- Misconfigured services
- Malicious code
- Public S3 buckets with sensitive data
Global Visibility
Our geo-location capability delivers contextual information identifying low, medium and high-risk areas for managing your infrastructure, network resources and other company assets.